Secure and Reliable Information Monitoring Through Cloud Solutions
In the ever-evolving landscape of data administration, the usage of cloud solutions has arised as a critical remedy for organizations seeking to fortify their information safety and security measures while simplifying operational efficiencies. universal cloud Service. The intricate interplay between guarding delicate info and making certain smooth availability poses a complex difficulty that companies have to navigate with diligence. By checking out the subtleties of safe and secure information monitoring via cloud solutions, a much deeper understanding of the technologies and techniques underpinning this standard shift can be introduced, clarifying the multifaceted benefits and factors to consider that shape the modern data management environment
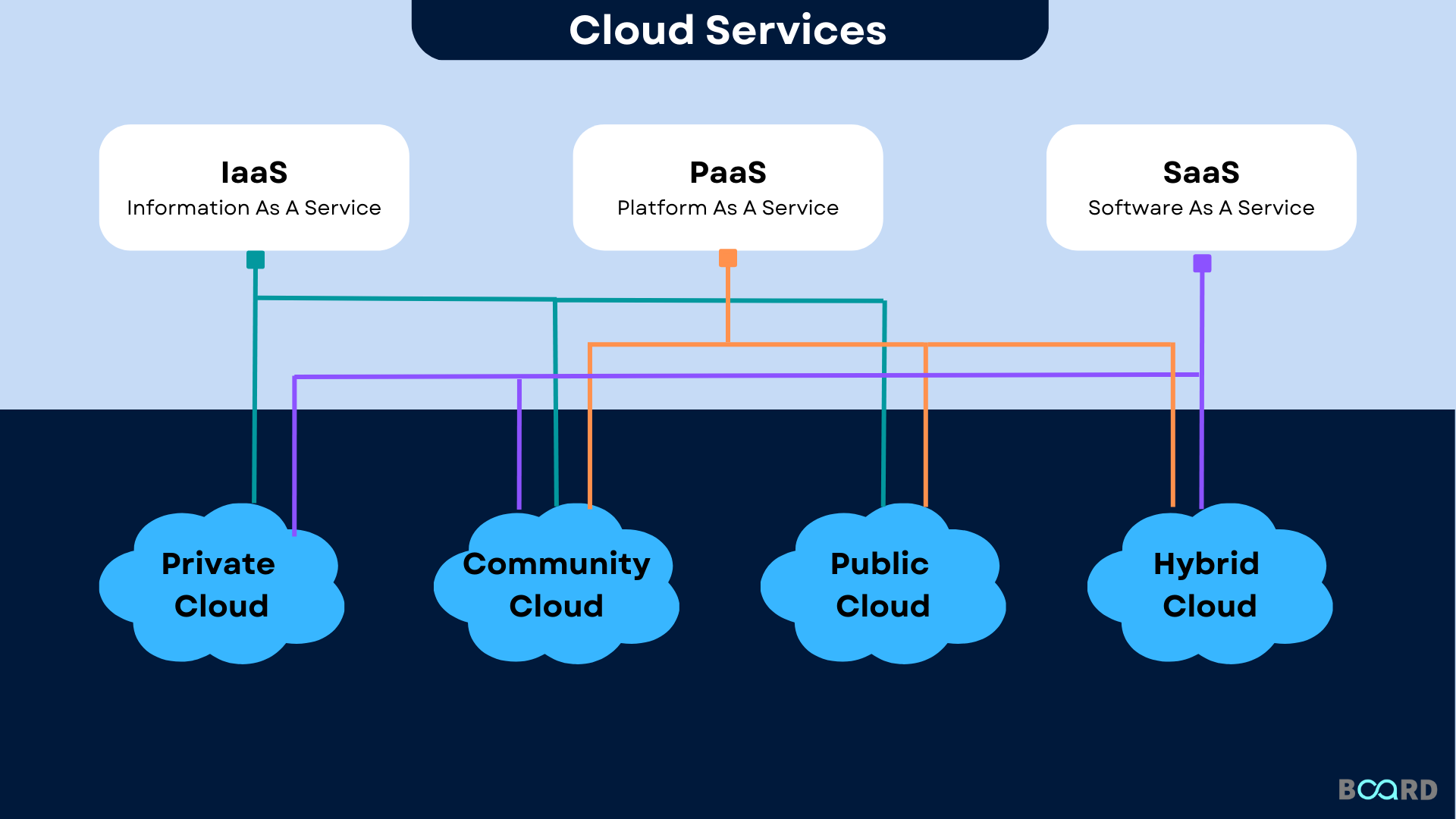
Significance of Cloud Solutions for Information Monitoring
Cloud services play an important duty in modern information monitoring methods due to their access, scalability, and cost-effectiveness. Additionally, cloud services offer high access, enabling users to access data from anywhere with a web connection.
Moreover, cloud services supply cost-effectiveness by getting rid of the demand for buying expensive hardware and upkeep. Organizations can choose for subscription-based designs that straighten with their spending plan and pay just for the resources they make use of. This aids in reducing ahead of time expenses and total functional expenses, making cloud services a feasible choice for services of all dimensions. In essence, the relevance of cloud services in data monitoring can not be overstated, as they offer the necessary devices to streamline procedures, enhance collaboration, and drive service growth.
Secret Security Challenges in Cloud Information Storage
To address these security challenges, companies require robust safety and security measures, consisting of file encryption, accessibility controls, routine protection audits, and staff training. Partnering with trusted cloud solution carriers that supply innovative protection features and conformity accreditations can additionally assist mitigate risks connected with cloud data storage. Inevitably, a aggressive and extensive approach to safety is essential in guarding data saved in the cloud.
Implementing Data Encryption in Cloud Solutions

Implementing information file encryption in cloud options involves utilizing durable file encryption algorithms and protected essential administration methods. Encryption keys must be saved separately from the encrypted information to add an added layer of defense. Furthermore, organizations need to on a regular basis upgrade security keys and utilize solid access controls to restrict who can decrypt the information.
In Resources addition, information file encryption must be applied not only during storage yet likewise during information transmission to and review from the cloud. Safe interaction procedures like SSL/TLS can aid protect information in transportation, guaranteeing end-to-end security. By focusing on information encryption in cloud options, organizations can reinforce their data protection pose and keep the privacy and integrity of their delicate details.
Best Practices for Information Back-up and Healing
In addition, carrying out regular recuperation drills is vital to test the performance of backup procedures and the company's capacity to recover information quickly. Automation of backup procedures can enhance operations and lower the potential for human mistake. File encryption of backed-up information includes an extra layer of safety and security, protecting sensitive info from unauthorized accessibility during storage space and transmission. By following these best techniques, services can enhance their information resilience and ensure smooth procedures despite unpredicted events.
Surveillance and Bookkeeping Information Gain Access To in Cloud
To keep data stability and protection within cloud environments, it is essential for organizations to develop durable measures for monitoring and auditing information access. Tracking information access entails monitoring that accesses the data, when they do so, and what actions they carry out. By applying monitoring mechanisms, organizations can discover any unapproved gain access to or uncommon tasks immediately, enabling them to take prompt activity to reduce possible threats. Auditing data gain access to goes an action additionally by supplying a detailed record of all information gain access to activities. This audit trail is important for conformity objectives, examinations, and recognizing any kind of patterns of dubious look at more info actions. Cloud solution carriers usually use devices and solutions that facilitate monitoring and auditing of information accessibility, permitting organizations to acquire insights right into just how their data is being used and making sure liability. universal cloud Service. By proactively monitoring and auditing data accessibility in the cloud, organizations can boost their total protection stance and keep control over their delicate info.
Verdict
To conclude, cloud solutions play a vital duty in making certain secure and effective information management for services. By attending to key safety and security obstacles via data file encryption, back-up, recovery, and monitoring techniques, organizations can safeguard delicate details from unapproved access and data violations. Implementing these best techniques in cloud services promotes data stability, confidentiality, and availability, inevitably enhancing collaboration and efficiency within the organization.
The crucial protection challenges in cloud data storage rotate around information violations, information loss, conformity regulations, and data residency worries. By encrypting information prior to it is posted to the cloud, companies can mitigate the risk of unauthorized access and data breaches. By prioritizing data encryption in cloud services, organizations can bolster their data security position and maintain the confidentiality and integrity of their sensitive information.
To maintain data honesty and security within cloud settings, it is important for organizations to establish durable measures for tracking and auditing data access. Cloud solution carriers typically use devices and solutions that assist in tracking and auditing of information gain access to, enabling companies to get insights right into just how their data is being utilized and ensuring liability.